Do you have a sense of security or real cybersecurity?
Businesses of all sizes are using MDR (Manage, Detect, Respond) to accomplish one goal: quickly identify new threats and limit an attacker’s occupy time within an environment.
“Are you struggling with the growing complexity of cybersecurity and finding a reliable cybersecurity partner? Are you having difficulty putting an efficient cybersecurity plan in place? Are you having trouble finding a trained cybersecurity expert? My name is Greg and I partner with companies of all sizes to solve these frustrating and dangerous problems. I offer straight talk, not tech talk. Let me show you how to get the cybersecurity posture you need. Enter your name and email in the box, and I’ll send you a series of 60 second methods that will show you how to get cybersecurity that is cost effective, not cost prohibitive. “
IT consultants, service providers and MSP’s, support many different parts of a security program, but detecting and responding to advanced threats is not where they specialize.
Focus on running your business, we will focus on the security.
Reduce Mean Time To Identify (MTTI)
Manage
Detect
Respond
Advanced threat management that helps visualize, detect and eliminate threats to the network in real-time.
We can give you deep insight and actionable intelligence into traffic across your network, as well as through the firewall, regardless of network size or design.
Real-time threat detection management and 24/7 response.
Analysis
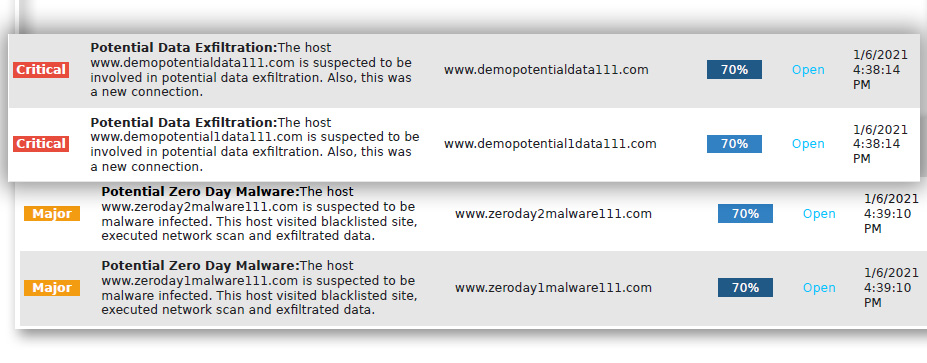
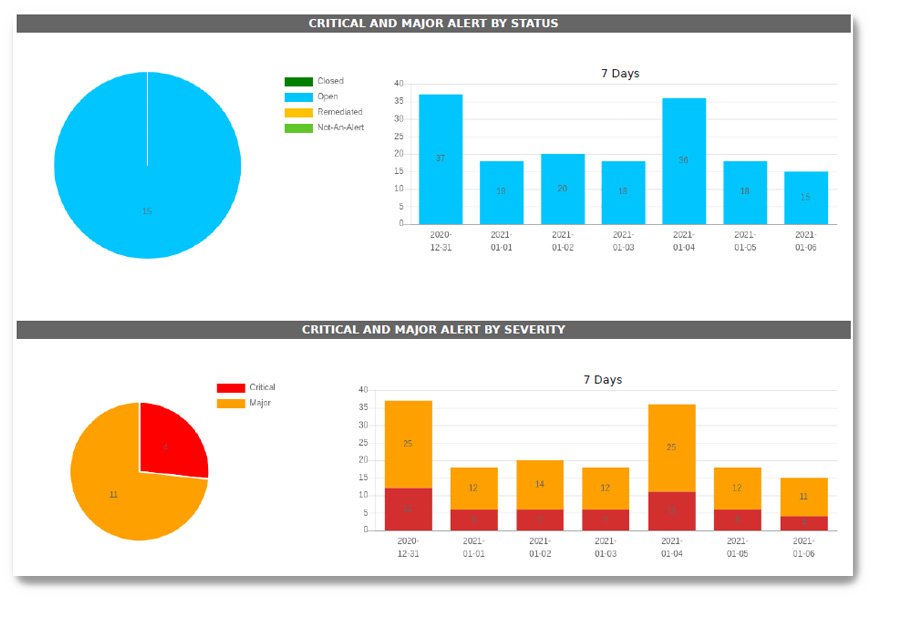
With 24/7 expert analysis, we remove false positives and only alert you to critical or major alerts.
Proactive alerts and actionable intelligence removing false positives.
FEATURES
Visibility
We monitor your environment by ingesting raw streaming data and Flows.
Logically auto discovers and creates asset groups.
Threat Detection
Machine learning and AI with actionable intelligence; eliminating need to add rules.
Behavioral analytics, predictive modeling and contextual real time alerts with automated analysis and correlation and elimination.
Threat Containment
Out of the box automated threat containment and elimination in real time.
Provides clear actionable steps to eliminate threats, which can be fully automated.
Compliance, Indexing and Reporting
Regulatory compliance (HIPAA, PCI, NIST, GDPR) assurance and customizable operational reports.
Log indexing , long term storage and data analytics for forensic analysis.
Operations Management
Microservice architecture facilitates rapid deployment across cloud, on premise or hybrid.
Simplified licensing based on the number of assets (versus that amount of data ingested).
Customized solutions
Every network is different. Our security engineers will assess your needs in a 1:1 consultation and design a custom configuration for your unique needs.
