
In today’s complex threat landscape, large-scale, multi-vector attacks now threaten the fabric of societies around the globe. Only the best security can protect against these Gen V attacks, and Check Point’s transformative new product innovations will achieve this better than ever.
Cynthetic Systems, an industry certified technical workforce that designs, implements the best security solutions for organizations in the Rocky Mountain region, is a 2 star partner of the Check Point SMB Security Suite.

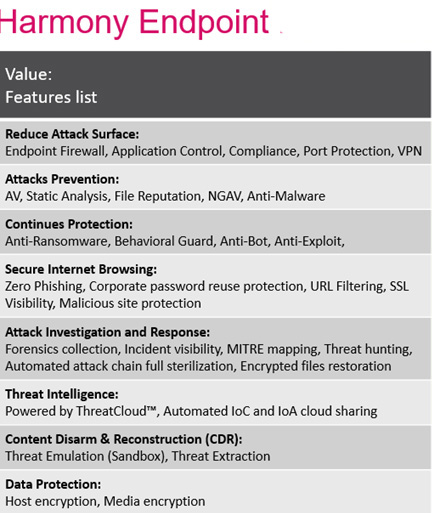


Check Point Harmony is the industry’s first unified security solution for users’ devices and access. It protects devices and internet connections from the most sophisticated attacks while ensuring zero-trust access to corporate applications. The Harmony product suite provides; Clientless Connectivity, Endpoint Security, VPN Remote Access, Mobile Security, Secure Internet Browsing, and Email Security.

The Check Point CloudGuard platform provides you cloud-native security, with advanced threat prevention for all your assets and workloads – in your public, private, hybrid or multi-cloud environment – providing you unified security to automate security everywhere. The CloudGuard product suite provides Cloud Network Threat Prevention, Cloud Security Posture Management, Web App & API Protection, Compute Protection (Containers & Serverless), Cloud Intelligence & Threat Hunting




