
82% of businesses underestimate their risk and don’t believe they are a target.
Cynthetic Systems enterprise-level security has more ways of protecting your high value business.
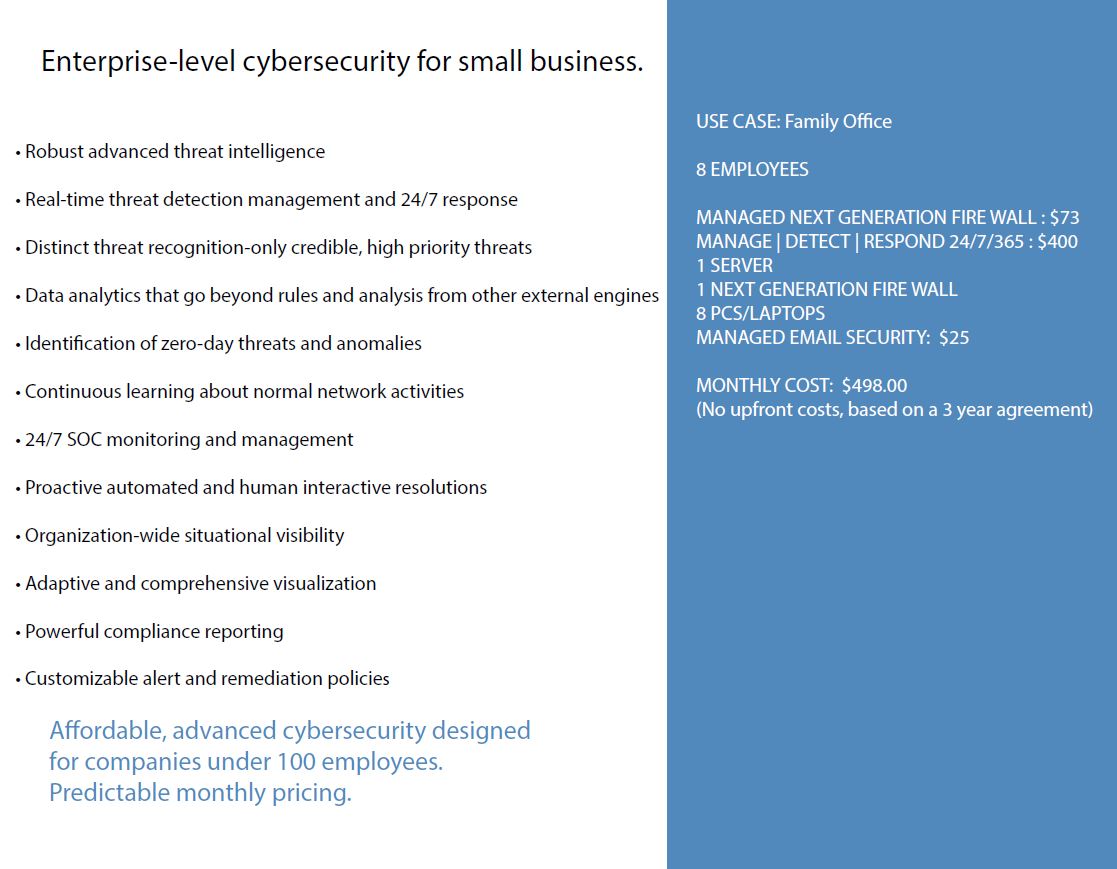
We are prepared to solve the challenges unique to Private Banking, Family Offices, HNWI, & VIPs.
24/7 Manage|Detect|Respond Cybersecurity
Cynthetic Systems MDR
CS MDR is an enterprise solution that scales from 1 to 1000 users. Our solution offers 24/7 monitoring, detection and response on premise, hybrid or in the cloud offering enterprise scale security for small organizations.
CS MDR gives you deep insight and actionable intelligence into traffic across your network, as well as through the firewall, regardless of network size or design.
Manage
Detect
Respond
Recognize the Threats to Your Business
Data Breaches
Personal information on your network is accessed, stolen, shared or used without permission.
Data Destruction
The loss of all the information on your business computing devices to malware, ransomware, user theft or error.
Phishing
When a criminal poses as a legitimate company to gain access to company financial data, typically through email.
Malware
Intrusion software designed to disable your computing devices, destroy data or hijack your networks. Mobile malware is on the rise.
Ransomware
Malicious software designed to block access to a computer or network until a ransom is paid.
Productivity Loss
Any successful attack can mean halting business as usual and losing customer trust.



Security Awareness initiatives can successfully mitigate the biggest security risk in your family office.
Security Awareness should include:
- Frequent, consistent and ever-evolving employee cybersecurity education
- Routine but unannounced penetration testing, particularly for phishing, downloads and telephone exploits
- Understanding and complying with established procedures, which could include everything from sites to avoid or which sanctioned apps or services to use
- Tiered ramification for non-compliance
- Using established best practices and training in the real world
Email is the top attack vector by far for hackers.
Our sound secure email solution includes dedicated, advanced-threat protection capabilities. The type of security offers protection against targeted phishing with malicious attachments and URLs, business email compromise (BEC), as well as impostor-based attacks.
24/7 managed firewall acts as a virtual perimeter wall for your business, helping prevent hackers from grabbing or destroying data.
Advanced firewall protection with United Threat Management (UTM) capability — matched to your Internet
connection speed and network size.
Download our 10 Steps to Secure Your Family Office Network Guide
